Download the content from the Microsoft Security Compliance Toolkit (click Download and select “Windows 10 Version 1909 and Windows Server Version 1909 Security Baseline.zip”). This new Windows Feature Update brings very few new Group Policy settings, which we list in the accompanying documentation. In response to direct customer need for a streamlined method of identifying common security misconfigurations, Microsoft has developed the Microsoft Baseline Security Analyzer (MBSA).
Microsoft’s Security Analyzer was once a decent tool that administrators could use to scan their systems and check for basic best practice settings. Since being discontinued, there’s been a hole that some admins are still looking to fill with a reliable security tool.
If you’re looking for a replacement, check our list of the top five alternatives to the Microsoft Baseline Security Analyzer (MBSA).
- SolarWinds Network Security Tools with Engineer’s Toolset (FREE TRIAL) An excellent set of tools designed specifically for network administrators and MSPs. The security tools in this bundle cover patching, network security, and real-time monitoring.
- Paessler PRTG Network Monitor (FREE TRIAL) Provides flexibility with sensors designed to scan any port or protocol.
- Intruder.io. A cloud-based network scanner whose goal is to make security simple and hands-off.
- OpenVAS. A powerful open-source scanner that’s backed by a large, active community.
- Nexpose. Offers quality network scanning, with full integration for the Metasploit framework.
1. SolarWinds Network Security Tools with Engineer’s Toolset (FREE TRIAL)
The Engineer’s Toolset is an administrator’s best friend and contains an entire suite of tools that can help you monitor your network, manage devices, and implement security measures. With that being said we’ll focus on just how useful the network security tools are for replacing Microsoft Baseline Security Analyzer.
Patch Manager is your one-stop-shop for managing Microsoft Windows updates, as well as keeping your third-party programs up to date. If you’ve used WSUS for patch management, you’ve likely experienced its shortcomings and run into plenty of limitations. Patch Manager was designed to fill that void by providing an intuitive patching dashboard, compliance reporting, and an array of pretested patching packages.
For real-time monitoring, Security Event Manager keeps sysadmins up to speed with all security-related events across the network. Security Event Manager features an easy to read dashboard that gives you a top-down view of outstanding issues at a glance. One of my favorite parts of this tool is its automated threat detection and response.
During configuration, you can set specific events or thresholds to trigger actions such as disabling a user account, removing permissions, or executing a custom script. This, of course, requires a bit of time to set up and test but eliminates the last minute panic when a security breach occurs.
Security Event Manager goes above and beyond what MBSA could ever do by providing a forensic breakdown of file monitoring and added elements of intrusion detection. Also, the tool kit comes with a tool you might not expect, an SNMP dictionary attack tool. Use this tool to simulate attacks on network devices to find flaws in your own security or weak passwords set by end-users. SolarWinds has compiled some of the most commonly used dictionaries for you to use out of the box but also allows for you to import your own, or even customize an existing dictionary.
All of these security tools plus more are conveniently bundled in the Engineer’s Toolset. You can test out any of these tools completely free for 14 days.
2. Paessler PRTG Network Monitor (FREE TRIAL)
If you’re looking for more flexibility with pricing and deployment, PRTG Network Monitor offers to monitor on a per sensor basis. For example, setting a monitor to listen for port traffic would count as one sensor. With PRTG you only pay for the sensors you use, giving you more granular control over what features you use, versus what you pay for.
Paessler takes a holistic approach by giving you the freedom to monitor many different types of protocols and traffic. If it exists, you can monitor it with PRTG. If you have very specific areas of security you’re looking to monitor, this makes PRTG an ideal solution.
In addition to monitoring, there are plenty of built-in mechanisms for notifications such as HTTP requests, push notifications, and email to keep you or your team in the loop on network and security events. Dependency settings help you dial down alerts to avoid flooding your ticketing system, while the scheduling section allows you to only let through critical alerts after hours.
If you’re looking to replace Microsoft Baseline Security Analyzer and also have some areas of your network that still need to be monitored, PRTGs broad scope of capabilities make it a great choice for any sized network. You can test out all of PRTG’s features with a free 30-day trial.

3. Intruder.io
Intruder.io is an entirely cloud-based scanner that is designed to find weaknesses and vulnerabilities in your network before the hackers do. Intruder utilizes similar external scanning that financial institutions use to ensure PCI compliance, and that best practices are being met. While Intruder isn’t reinventing the wheel, it does a good job delivering you actionable reports on areas of weakness prioritized by the level of impact it could have on your network.
When a threat or missing patch is found, you can receive an alert to be notified as soon as it’s found. Alerts are also integrated into Slack and Jira, making this an ideal tool if your team works with one of those apps.
Intruder is definitely marketed towards those who aren’t tech-savvy and lacks the ability for you to customize attack vectors, ports, or any of the fine details most tools allow for. If you’re looking for the most hands-off approach to threat prevention and monitoring, Intruder is a solid option. Of course, all of this convenience comes at a price. The base monthly fee starts at $94.00 (62.92) when billed annually, plus a per target fee starting at $2.70 (2.15) per target you wish to scan.
4. OpenVAS
OpenVAS is an open-source and completely free vulnerability scanner that was first published in 2009. Much of the power behind OpenVAS comes from the community where you’ll find more than 50,000 different types of vulnerability tests you can run through the software.
The flexibility and power of OpenVAS are only limited to your imagination and skillset. With that being said, as with most open-source products your support will be limited to the community forums, and what you can piece together across Google searches.
While not much about OpenVAS is plug and play, you’ll find yourself with a rudimentary dashboard displaying the number of tasks you have running. Also, your CVEs that are created over time, and a pie chart view of the number of current threats found based on severity.
Once a scan is finished, you’ll have the chance to view what was found under the results tab. Here you’ll see a list of the type of vulnerabilities that were found, what their severity rating is, and the corresponding port number and service that encompasses it.
Drilling down into the results you’ll be given a fairly technical summary of how the attack was carried out and how your system reacted to that attack. Below this, the scan provides the next steps to mitigate this type of attack. Sometimes this is as easy as changing a password, other times it can involve numerous steps. I was pleasantly surprised by the level of detail provided in this section.
Although there are a vast amount of documentation and use case examples in the Knowledge Base, I found there is still a fairly steep learning curve for utilizing OpenVAS to its full potential.
The level of customization you apply to OpenVAS is extremely high given the fact the entire tool itself is open source. You might find this ideal if you’re looking to scan very specific ports and protocols on custom applications or other non-conventional programs.
For most corporate environments, OpenVAS will likely be too much to learn and take too long to be worth the effort. But for those who are on a budget and have the time and dedication to really learn OpenVAS, this could be the alternative to Microsoft Baseline Security Analyzer you’ve been looking for.
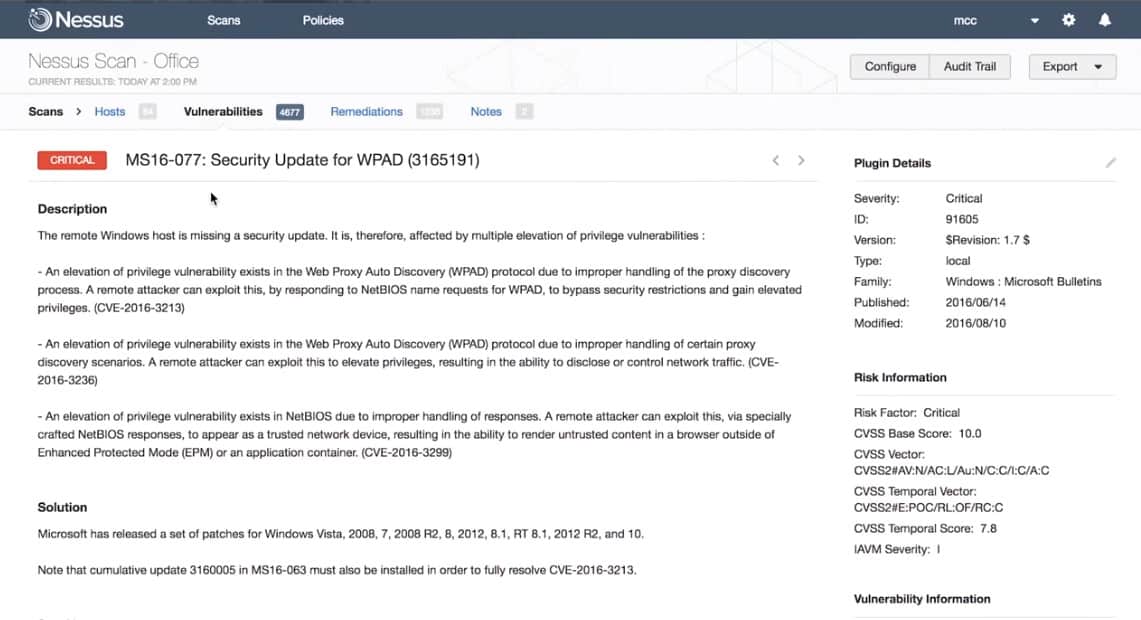
5. Nexpose
Nexpose is an on-premises security scanner developed by Rapid7, the same company that developed the popular offensive security tool Metasploit. One feature that sets Nexpose apart from the other tools is its Real Risk Score system.
Nexpose finds and scores threats on a 1-10 scale taking into account the vulnerability’s age, number of public exploits that are available, and the chance that an attack would actually be successful. This level of insight gives you a quantitative look at just how you should prioritize your patching and threat mitigation.
On the active side of your network, Nexpose can be configured to immediately detect new devices on your network and scan them. Rather than relying on infrequent data dumps and definition updates, Nexpose’s ‘Adaptive Security” taps into its Sonar Project to find and compare your results to some of those latest threat discoveries.
In addition to basic network scanning, you can also configure Nexpose on a policy level to help your network stay compliant with standards like PCI, NIST, and CIS. These policy templates come preconfigured and only need to be launched to run. When the scan is complete, a report gives you step by step instructions on what needs to be done starting with the actions that will make the biggest difference in terms of compliance.

Since this tool was created by the same team that worked on Metasploit, you can expect a full-on integration with the Metasploit framework. While this integration may be more than what most companies need, it makes a perfect pair for admins who are looking to simulate a breach and play on the offensive side to test their network.
Lastly, all of this data is compiled in a remediation report that’s pre-designed to be ready to hand off to executives and other individuals that just need a high-level overview of the results. The report does a great job of staying simple, yet informative. A large letter grade is marked in the top left-hand corner to give an immediate indication of your network’s standing.
You can test out all of the features Nexpose has to offer free for a full 30-days.
Choosing a MBSA Alternative
It’s clear that Microsoft Baseline Security Analyzer is outdated and doesn’t fit most organizations’ needs anymore. While we’ve listed the best alternatives to MBSA, we’ve found a few tools that work especially well depending on your company’s size and requirements.

Managed service providers and most medium-sized businesses will greatly benefit from SolarWinds Engineer’s Toolset. Not only will these tools replace the functionality of MBSA, but they’ll also provide even further protection through streamlined automation and solutions you can implement right out of the box.
For similar-sized organizations who need more control over their budget, PRTG per sensor pricing might be a better fit depending on how many devices and services you need to monitor. You’ll find that PRTG can integrate and monitor nearly any service or protocol available, so if you’re looking for monitoring beyond just security PRTG could be a wise choice for your organization.
Microsoft Baseline Security Analyzer Alternative
Lastly, for businesses that have more time than money, OpenVAS is a free and open-source scanner that can be configured in almost an unlimited number of ways. Just make sure you have the time to invest in mastering it, as there is little to no support beyond the community.
So what’s your favorite alternative to MBSA? Be sure to let us know your favorite tool in the comments below.
Summary
‘After MBSA analyzes the system for security vulnerabilities, a report is created as a plain text file that includes sensitive information that can be used by hackers to attack the specific machine. MBSA was created to help users become aware of risks and available patches. However, MBSA turns the simple vulnerability of reading local files into a much more powerful vulnerability. Such a simple vulnerability allows potential hackers to find out about vulnerabilities that enable full control over the machine that is under attack. These are automatic attacks.
This means that active content (executables, scripts, ActiveX, Java, etc.) has the ability to generate a list of vulnerabilities or read a previously created list, and can then utilize these vulnerabilities to its advantage. Even if this report can be accessed only by a specific user, the active content can access it too.’
Microsoft Baseline Security Analyzer Replacement
Credit:
‘The information has been provided by Menashe Eliezer.’
Details
‘Vulnerable Software:
Microsoft Baseline Security Analyzer (MBSA) 1.0
Mitigating factors:
If the report is located in an NTFS partition, only the user can access it. However, any active content is launched with user permissions and can read this information. Such attack will not be automatic on fully patched machines with default security settings selected. However, many machines are not so ‘resistant’.
Overview:
Microsoft released Baseline Security Analyzer on April 8, 2002. The Microsoft Baseline Security Analyzer (MBSA) analyzes Windows systems for common security mis-configurations. Version 1.0 of MBSA includes a graphical and command line interface that can perform local or remote scans of Windows systems. MBSA runs on Windows 2000 and Windows XP systems and will scan for missing Hotfixes and vulnerabilities in main Microsoft’s products. More information can be found at:
http://www.microsoft.com/technet/treeview/default.asp?url=/technet/security/tools/Tools/mbsahome.asp
Technical overview:
MBSA creates a report that includes sensitive information that can be used by hackers and save them research time. The report can be accessed by a malicious active content:
1. The report is written to a known folder, e.g., C:Documents and SettingsusernameSecurityScans. The user cannot change this location.
2. The XML report is written in plain text and can be used by hackers to find the machine’s vulnerabilities.
The problem is not the option of the automatic attack, even though new exploits are published quite often. Users often do not follow Microsoft’s advice regarding security patches and security settings. Even a user with a fully patched version of IE may choose to trust certain active content and launch it.
It is very easy to write malicious active content that will access the MBSA report. We do not believe that IE should be changed. Active content risks are known (and can be handled by Finjan’s behavior-inspection applications).
Ways of delivery:
There are many ways to deliver such active content. For example:
1. Embedded in a web page and utilizing low security settings for the browser, or on the user’s acceptance of the object.
2. Embedded in a HTML-formatted e-mail
3. E-mail attachments.
4. Executable downloads.
Examples of active content that access the file system can be found at: http://www.finjan.com/mcrc/sec_test.cfm (If you are using one of Finjan’s behavior-based security products, please disable it before running these demos)
Some attacks will be automatic if the browser’s security setting is low, for example, the Java, and the ActiveX demos at the above test site. Based on our disclosure policy, we have not written a specific demo for demonstrating this risk, but it would be quite simple to do so.
We had an interesting discussion with Microsoft about this exploit, and their response is quoted in the bottom of this alert.
Finjan Software warns that this exploit may be used in the wild, and strongly advises you to take proper precautions to protect yourself from this type of attack. Finjan products block this exploit by offering the only solution that proactively inspects active content behavior both in gateway and in desktop level. (Based on two different patented technologies)
Vendor response:
Finjan Malicious Code Research Center had an interesting discussion with Microsoft Security Response Center. This is their response:
Hi, Thanks very much for your note and for sending this on. We really appreciate it. To understand the issue fully, it would be good to expand this somewhat. There really are two issues here: One related to the ability to mount an attack successfully, and one related to how data is stored on a system and what could happen to that in light of a successful attack. To be clear, none of the attack scenarios that you’ve described are mounted through MBSA itself. Also, the attack you’ve described does not exploit a vulnerability in any product: in a default system this attack fails. It’s only when a user chooses to run code from an untrusted source and proceed despite the security warnings provided that this attack could succeed. Protecting systems against untrusted code is vitally important, and we call this out in our 10 Immutable Laws of Security as Law #1 ( http://www.microsoft.com/technet/columns/security/10imlaws.asp ), to underscore its importance. If an attacker were able to convince a user to run their code, that code would then be able to take any actions on the system that the user can take. While it is true that MBSA stores its information in a known location, storing it in an unpredictable location would not measurably change the situation. An attacker’s code could just as easily search the local system for the file. Likewise, it is true that MBSA’s information can be read by the user (or code running as the user). However, even if the MBSA information were not present on the system, code running as the user would be able to determine the presence or absence of patches, simply by consulting the time/date information contained in the publicly available MSSecure XML database. Again, it is a question of degree rather than feasibility. The larger issue in both cases is the presence of code running with the user’s privileges. If the attacker cannot run code, it does not matter how the MBSA data is stored, because the attacker cannot access it. If the attacker can run code, he or she does not need the MBSA data, as they already have all the privileges needed to duplicate the MBSA processing. (For that matter, the attacker could simply run MBSA itself and do a ‘screen scrape’). That said, we are always looking to make improvements and we appreciate concerns and feedback like this. Our MBSA team is looking at these suggestions along with others that we have received and consider them as they design future versions of this tool.
Thanks again for sending this on, we really appreciate it.
Regards,
secure@microsoft.com‘